
Site Search
Redefining Cybersecurity for Software Projects with Web Application Security Solutions

Table of contents

Let's talk
Reach out, we'd love to hear from you!
Web application security has consistently remained at the forefront of concern. Perpetrators continuously engage in the exploration of potential vulnerabilities within development environments, deployment infrastructure, third-party APIs, and open-source dependencies.
The integration of security measures is no longer a secondary consideration within software development projects. As malicious tactics continue to evolve, the implementation of robust cybersecurity measures has become an imperative for both established enterprises and emerging startups.
According to a projection by Statista, cyberattacks such as network intrusion, distributed denial-of-service (DDoS) attacks, phishing scams, ransomware incidents, and man-in-the-middle (MitM) attacks are anticipated to inflict a financial toll exceeding $452 billion upon businesses based in the United States. These attacks not only result in significant periods of operational downtime but also inflict reputational harm upon the affected organizations.

Although awareness about cyber security has increased, the rate of security breaches reached alarming levels in 2023. Here are a couple of notable data breaches, which indicate that no company is immune to hacking attacks.
In November 2023, Samsung’s customer information was breached because of a third-party app vulnerability that affected UK-based users who used the app to make online purchases in 2020. This led to unauthorized access to personal information like names, phone numbers, emails and home addresses.
In October 2023, Walmart’s data breach was reported, with 85,000 individuals being affected by a cyber attack. It exposed protected health information like patient names, dates of birth, and prescription data. Walmart informed its customers of the attack and reported the incident to the U.S. Department of Health and Human Services Office for Civil Rights in October, yet all detailed information about the breach remained undisclosed.
However, all is not lost. Development and security teams in software development companies around the world are implementing protection methods for safeguarding sensitive data.
What is Web Application Security: Understanding the Fundamentals from the Ground Up
Web application security safeguards application data and code from cyberattacks and data breaches. It encompasses security measures at each phase of the software application development lifecycle (SDLC), including design, development, and deployment.
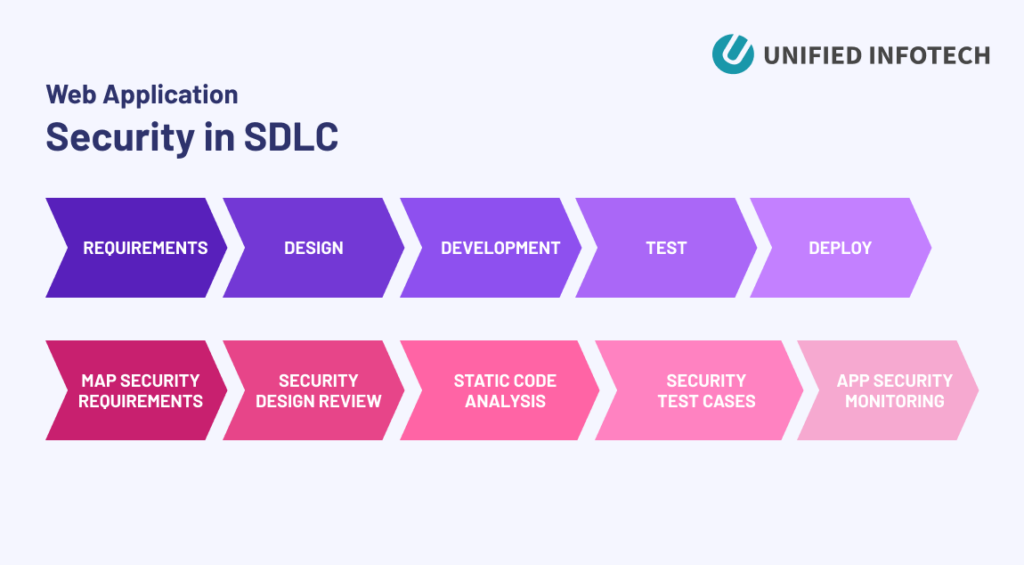
It entails the implementation of methods to identify and mitigate security vulnerabilities, reducing the risk of attacks. The most commonly used countermeasures and security controls in software projects include:
- Automated static code analysis
- Security testing of new software releases
- Use of application firewalls to define and enforce activities
- Encryption and decryption programs
- Biometric authentication systems
Security Risks Your Web Application May Face
Web applications encounter various attack types based on attacker goals, the nature of work performed in your organization, and its security gaps. These include:
- Zero-day Vulnerabilities: Attackers exploit system vulnerabilities that are known but not yet patched.
- Cross-Site Scripting (XSS): Injects client-side scripts to access or manipulate user data.
- SQL Injection (SQLi): Exploits database query vulnerabilities to access or modify data.
- Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS): Overloads servers with attack traffic.
- Memory Corruption: Unintentional memory modification exploited for malicious behavior.
- Buffer Overflow: Overwrites adjacent memory locations, enabling code injection.
- Cross-Site Request Forgery (CSRF): Triggers unauthorized requests using the victim’s credentials.
- Credential Stuffing: Uses automated scripts to input stolen credentials from one breach to attempt to gain unauthorized access to another website.
- Unauthorized Page Scraping: Bots steal webpage content for various malicious purposes.
- API Abuse: Exploits vulnerabilities in APIs to intercept data or inject code.
- Undocumented/Unapproved APIs: Undisclosed APIs expose sensitive data without security oversight.
- Misuse of Third-Party Libraries: Vulnerabilities in third-party tools compromise data processing.
- Attack Surface Misconfigurations: Unintended vulnerabilities due to oversight or misconfigurations like misconfigured logging, disabled security controls, lack of encryption, improper versioning, and excess privileges.
8 Strategies that Ensure the Security of Your Web Application
By implementing the following fundamental web application security services, you can effectively bolster the defenses of your organization against evolving cyber threats.
- DDoS Mitigation: Safeguarding against overwhelming malicious traffic by deploying specialized filtration and high-bandwidth capacity solutions.
- Web Application Firewall (WAF): Filtering out potential threats and exploiting web application vulnerabilities is crucial in rapidly evolving threat environments.
- API Gateways: Identifying and blocking traffic targeting API vulnerabilities while managing and monitoring API traffic effectively.
- DNSSEC: Ensuring secure DNS traffic routing to prevent interception by attackers.
- Encryption Certificate Management: Outsourcing SSL/TLS encryption processes to manage private keys, certificate renewal, and revocation efficiently.
- Bot Management: Utilizing machine learning to distinguish human users from automated traffic and prevent unauthorized access.
- Client-Side Security: Monitoring third-party JavaScript dependencies and code changes to detect and prevent malicious activities.
- Attack Surface Management: Providing centralized tools to map, identify, and mitigate security risks across the attack surface.
Leverage the Benefits of Web Application Security Best Practices Employed by Unified Infotech
Cybersecurity is an actual business enabler! Our team of web application development engineers has the expertise to fortify software applications against unauthorized access, data breaches, and malicious activities.
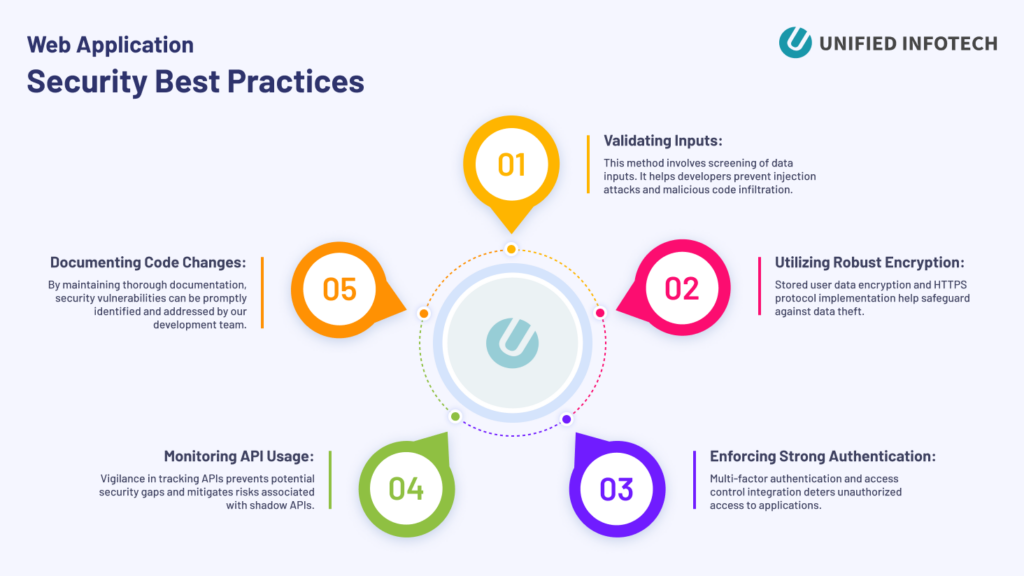
The software developers adopt the following protective countermeasures against prevalent security risks outlined by the OWASP Top 10 list:
- Validating Inputs: This method involves screening of data inputs. It helps developers prevent injection attacks and malicious code infiltration.
- Utilizing Robust Encryption: Stored user data encryption and HTTPS protocol implementation help safeguard against data theft.
- Enforcing Strong Authentication: Multi-factor authentication and access control integration deter unauthorized access to applications.
- Monitoring API Usage: Vigilance in tracking APIs prevents potential security gaps and mitigates risks associated with shadow APIs.
- Documenting Code Changes: By maintaining thorough documentation, our development team can promptly identify and address security vulnerabilities.
Ensuring Enterprise-Grade Application Security: How do We Use Threat Modeling to Build Security into Software Development Projects
Threat Modeling is the process of protecting sensitive information, software applications, and business operations. It uses system diagrams, hypothetical situations, and vulnerability testing. We incorporate Threat Modeling into our DevOps process. This prevents common cybersecurity problems like improper error handling, missing data encryption, weak input validation, and poor authentication.
It enhances cybersecurity and fosters trust in critical business systems. Our web application security engineers pinpoint vulnerabilities, conduct risk assessments, and recommend corrective measures. The process involves creating data flow diagrams (DFDs) and visualizing attack paths, while prioritizing assets and risks. This enables our software application development team to grasp network security and architecture comprehensively.
Some common examples of Threat Modeling methods and tools include attack tree, trike, CIA method, VAST, LINDDUN, and STRIDE frameworks.
Web Application Security Testing – The Key to Finding Security Vulnerabilities
Web security testing seeks out security vulnerabilities in Web applications and their setup, primarily focusing on the application layer. This involves sending various inputs to provoke errors and assess unexpected behavior. These software testing methodologies, sometimes considered as negative tests, evaluate whether the system or software application is performing any unintended actions.
Importantly, web application security testing is not solely about testing security features like authentication and authorization. It also involves ensuring other features, such as business logic and input validation, are implemented securely. The objective is to verify that all functions exposed in the web applications are secure.
Types of Web Application Security Solutions and Tools We Employ
- Static Application Security Testing (SAST): Detects code flaws by analyzing source files. This allows for quick detection and collaborative troubleshooting.
- Dynamic Application Security Testing (DAST): Proactively simulates security breaches. It helps to identify exploitable flaws and evaluate applications in production for runtime errors.
- Interactive Application Security Testing (IAST): Combines SAST and DAST elements. It enables real-time analysis within the application for accurate results.
- Runtime Application Security Protection (RASP): Continuously monitors applications for security breaches. It alerts our IT team by automatically responding to threats and terminating suspicious sessions.
- Mobile Application Security Testing (MAST): Assesses mobile app security through static and dynamic analysis. This helps to identify issues like malicious networks and data leakage.
- Web Application Firewall (WAF): Filters HTTP traffic to protect against various attacks like XSS and SQLi, functioning as part of a holistic security stack.
- Cloud Native Application Protection Platform (CNAPP): Centralizes control of cloud-native application security tools. technologies like CSPM, CWPP, and API discovery for comprehensive security management.
Wrapping Up
Cybersecurity is an essential part of a comprehensive software security program. Unified Infotech collaborates with you to safeguard your business through advanced cybersecurity solutions and web application security services. Our innovative security approach incorporates zero trust principles, empowering you to thrive amidst uncertainty and cyber threats.
We assist you in effectively managing and mitigating risks and vulnerabilities in today’s cloud environments. Our developers integrate solutions to safeguard your digital assets, sensitive data, and digital users against evolving threats.
Leverage the latest cloud-based cybersecurity solutions to bolster your access management, network security, and endpoint security across various devices and infrastructure.

Frequently Asked Questions (FAQs)
Why should I choose Unified Infotech for my custom software development project?
Unified Infotech, a trusted digital transformation partner, specializes in tech-agnostic custom solutions tailored to your unique business needs, making us the ideal choice for your custom software development project. Our customer-first approach prioritizes your goals, ensuring that everything we develop aligns with your vision and business requirements. Our team’s proficiency in a wide range of technologies ensures tech-agnostic outcomes and guarantees the best tools are selected for your project. With a proven track record of successful projects across multiple verticals and industries, we bring reliability and expertise to the table while maximizing cost savings.
What is custom software development, and how is it different from off-the-shelf solutions?
Developing custom software means creating a solution tailored to your business requirements and long-term goals. Unlike off-the-shelf software, custom solutions are built around your unique challenges and objectives. This results in greater efficiency, scalability, and alignment with business objectives. Custom software allows for complete control over functionality, ensuring it evolves with your business. In contrast, off-the-shelf solutions often require compromises and may lack the flexibility to adapt to specific requirements, making custom software a more strategic long-term investment.
For more clarity, read our infographic on Custom Web Development vs. Standardized Templates for business websites.
How do I identify the right tech stack for my custom software application development requirements?
When it comes to choosing the tech stack, we delve deep into several factors - the existing platforms, infrastructure of the client, scalability, data types, and so on. The specific requirements and features expected from the software application play a major role in making this decision.


